Identifying and Reporting Cybersecurity Incidents
CSI: Cybersecurity Investigators
Knowing how to identify a potential cyber-attack has seemingly become a job requirement nowadays for anyone working with technology in any k-12 school district. But with so many devices, services, and solutions that make up our technology environment, monitoring every asset 24/7 has become an impractical if not impossible task. However, knowing what to look for when evaluating a potential cybersecurity incident and being prepared to handle a cybersecurity incident so we can act quickly and effectively when it matters the most.
The Scene of the Crime
Cybersecurity incidents are a lot like crime scenes, with the attacker leaving evidence of the incident behind. From this evidence left behind, security researchers over time have been able to piece together attack methods and techniques to help us identify cybersecurity incidents and attacks before they are successful. One such way is the Cyber Kill Chain. The Cyber Kill Chain is a framework, created by Lockheed Martin, that is used for the identification and prevention of cyber intrusions activity. The model identifies what the adversaries must complete in order to achieve their objective. This framework consists of seven steps: Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and control, and Actions on objectives. These steps are then used to analyze the adversary’s tactics, techniques, and procedures to understand where they have been and where they are headed. For more information on the Cyber Kill Chain check out the Lockheed Martin Cyber Kill Chain Website.
Identifying Threats: What to Look For
The Cyber Kill Chain is a great resource to use when responding to an incident and determining how the attacker has infiltrated the network but what if we haven’t discovered the incident yet? The good news is that there is even more evidence that has been gathered that we can use to discover or prevent a cybersecurity incident from happening. By analyzing behavior patterns and looking for an anomalous or suspicious activity we can effectively target and respond to any threat that may be lurking on our network.
When analyzing behavior patterns, one of the most important things to look for is unusual behavior patterns in your environment. This could be unusual behavior from privileged user accounts (admin accounts, domain admin accounts, district administration accounts, etc.), unauthorized insiders trying to access servers and data (ie. a teacher account trying to access payroll accounts, servers, or services), anomalies in outbound network traffic (network traffic going out to different countries like Russia or China), abnormal browsing behavior or traffic sent to or from unknown locations. Oftentimes these behaviors can be indicators that there is activity on our network or in our environment that could be malicious and should be investigated further. When investigating these behaviors it is important to look for excessive memory or disk consumption, changes in configuration, hidden files, unexpected changes, and suspicious registry entries as these could be key indicators that a potential cybersecurity incident is underway.
Common Attack Methods and Remediation
As you can see from this small non-exhaustive list there is no “one size fits all” approach to identifying and investigating cybersecurity incidents. Every incident is unique and while one behavior pattern might work well for spotting a certain type of cybersecurity incident it might work as well for a different type of incident. From the behaviors listed above, we have put together some different attack methods to best illustrate how you might identify and remediate some of the most common types of attacks that we face in our k-12 environments.
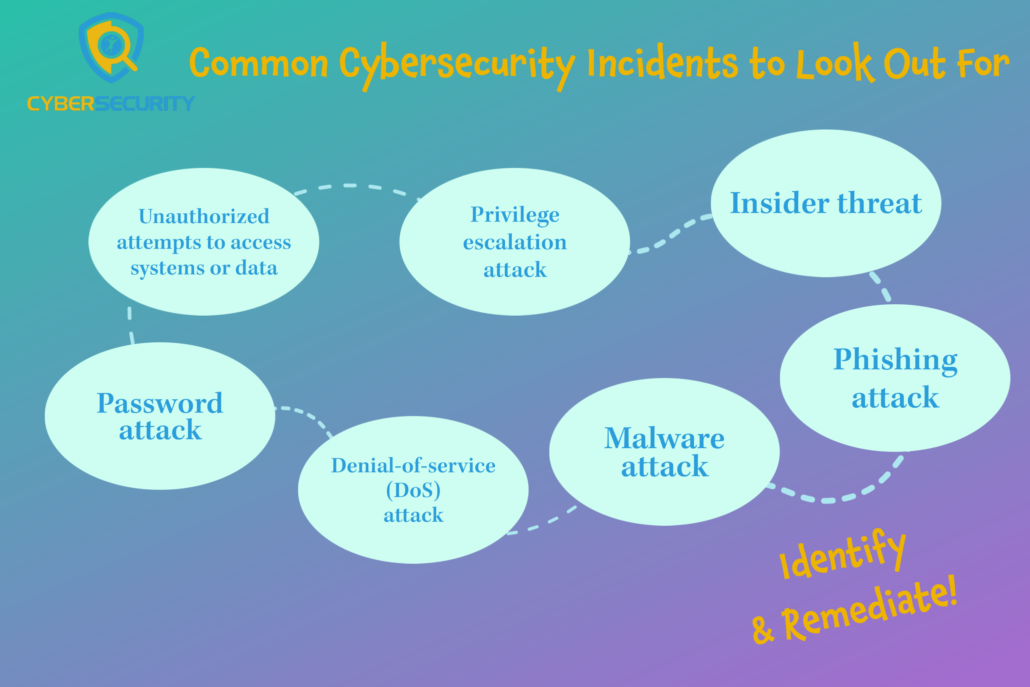
Unauthorized attempts to access systems or data: To stop an attacker from getting access to accounts or data it is important to implement 2-factor authentication. 2-factor authentication, while not “unhackable”, presents the attacker with a barrier that cannot be easily bypassed even if they were successful in compromising a user’s password. Data encryption should also be used to protect sensitive data at rest and in transit.
Privilege escalation attack: An attacker who attempts to gain unauthorized access to an organization’s network may then try to obtain higher-level privileges using what’s known as a privilege escalation exploit. Successful privilege escalation attacks grant threat actors privileges that normal users don’t have. By using the principle of least privilege, limiting the access rights for users to the bare minimum permissions they need to do their jobs, we can reduce the number of privileged accounts available for an attacker to escalate.
Insider threat: By using antivirus/endpoint detection and response software and firewalls we can prevent easy exfiltration of data by a disgruntled former employee. Using these tools we can also enforce stricter rules on the use of removable media(flash drives or thumb drives, etc.) which may be used to exfiltrate the data.
Phishing attack: Phishing attacks are the most common attacks our district will see and are often revealed by suspicious email traffic only after it’s too late. User awareness training is the most effective way to prevent this kind of attack along with email gateway filtering by implementing DKIM, SPF, and DMARC records.
Malware attacks: Signs of malware include unusual system activity, such as a sudden loss of disk space; unusually slow speeds; repeated crashes or freezes; an increase in unwanted internet activity; and pop-up advertisements. Installing an antivirus/endpoint detection and response tool can detect and remove malware. These tools can either provide real-time protection or detect and remove malware by executing routine system scans.
Denial-of-service (DoS) attack: A DoS attack is usually seen as a flood of incoming network traffic that either resolves or does not resolve to deny service to a particular site, service, or device. These attacks are commonly seen on internet-facing servers or Access Points on the network. To avoid these attacks make sure that DoS protections are enabled on all network switches.
Password attack: Password attacks can be password brute-forcing, password spraying, or password cracking. Oftentimes if a password attack is being carried out against your network you will see an abnormal amount of high failed password attempts against one or several accounts. To prevent these attacks 2-factor authentication is recommended as well as password lockout policies that will lockout an account after so many failed login attempts.
Be Prepared: The Importance of an Incident Response Plan
The importance of being prepared can not be stated enough when talking about a potential cybersecurity incident. The faster you can investigate and respond to a potential threat the less likely it is for that potential threat to accomplish its mission or task. One way to be prepared is to have an escalation process that allows someone to escalate an issue to the proper person to investigate that issue before it becomes an incident. But, to be the most prepared that your district can be, a Cybersecurity Incident Response plan should be a document that you have in both a digital and physical copy. This plan can be as generic or specific as you would like but outlines some key items such as who to report incidents to, who investigates the incidents, who communicates that an incident has occurred, and a general playbook of an investigation and remediation procedure and timeline. A good incident response plan not only will save you valuable time and maybe even your network when an incident happens.
Staying Vigilant in the Face of Threats
Over the last couple of years, most cybersecurity researchers believe that is no longer a case of “if” something will happen but rather “when” as it relates to cybersecurity incidents or attacks. With this in mind, it is more important than ever to know and understand how to identify and report a cybersecurity incident. Between utilizing attacker frameworks and methods, analyzing unusual behavior patterns, and being prepared with an incident response plan, we can confidently defend our district’s networks and keep the attackers at bay.
Learn More
For more information on how to best protect your district from a Cybersecurity incident, contact us to schedule an Assessment!
